Who spies on your car — other than you?
By Thom Cannell
Senior Editor
Michigan Bureau
The Auto Channel
LANSING, MI: Today I got another notice my personal information had been stolen. You too? Mortgage company, health care system, phone company, department store, bank, and more? What about your car, did it get hacked? Yes, your car, your semi-tractor or even a John Deere harvester can be hacked for data, or worse.
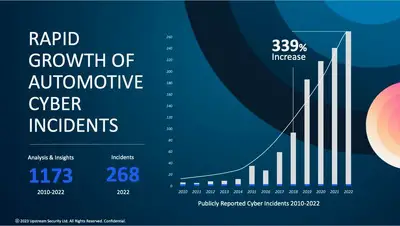
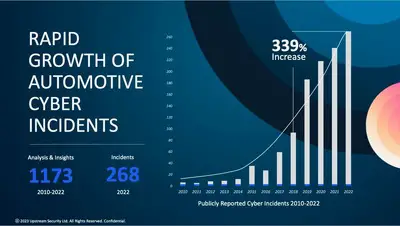
The first publicized vehicle take-over was of a Jeep Cherokee in 2017. Cyber criminals have become more menacing, their skills and technology significantly upgraded since Charlie Miller and Chris Valasek performed that exploit. What took three years may now be available over the counter.
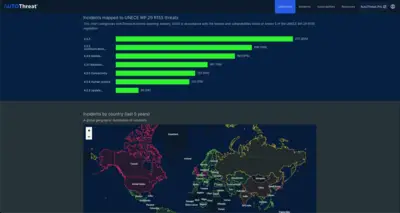
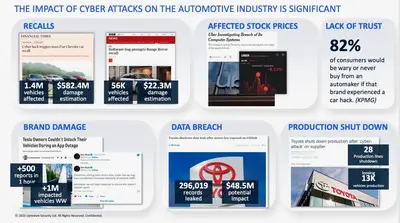
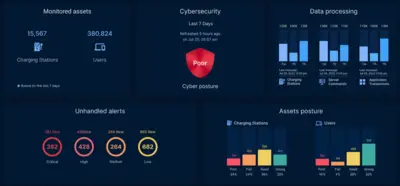
Upstream, a company developed to combat such evil says four competitive car manufacturers, insurance companies and others are investors due to the necessity of cyber security; the industry lost an estimated $505 billion dollars 2019-2023. Upstream monitors, in real time, hacker activity to deduce current and emerging cyber threats and now protects over 25-million vehicles. Of course it’s the wealthy companies that are targeted, primarily with the threat of ransomware and what you see in the media represent only 10% of the problem.
You’re saying, “Nah, not me, I’m safe!”
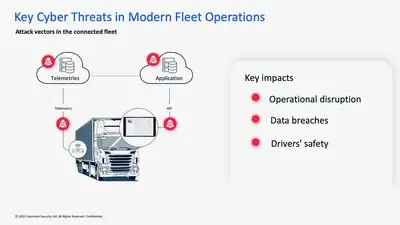
If your vehicle is connected; SiriusXM satellite radio, over-the-air updates, automatic crash reporting, Pandora or Spotify on your infotainment screen, if you can use a mobile phone to unlock your vehicle, if your vehicle has a SIM card and modem that processes data, and most built in the last decade(s) do, you are at risk.
Fraud and theft are, day by day, increasing with everything now controlled by software in the vehicle, in the cloud and in fleets. For instance, Russia stole a fleet of agricultural vehicles from Ukraine and Ukraine promptly disabled the vehicles remotely, preventing their use. 25 Teslas were targeted and owners disenfranchised. A hacker found an entry to 15,000,000 vehicles from three manufacturers and needed only a VIN to affect selected models. Vehicles are vulnerable on many layers; the vehicle itself, its data/telematics, even the manufacturer’s cloud or sales, service, finance and warranty data.
Your data is sensitive, your routes, dates and times. Vehicles can be stolen with cyber techniques, inexpensive black boxes that can open and operate many vehicle models. Let’s say you purchase and download an app that starts the car, turns on the A/C, changes current driver settings. What if somebody hacks that app? They then control the vehicle and can remove you from ownership. Fleets are vulnerable to ransomeware—think UPS, FedX, Amazon, especially at Christmas. What about Hertz/Avis or Brinks and other bank service providers? So far, fleets may have escaped—that we know of.
Fraud, stealing cars, locating and stealing cargo and data theft is accompanied by fraudulent warranty claims. Today, odometer mileage is rolled back with cyber tools, not a drill motor, to impact lease over-mileage payments and mileage-limited warranty claims. In the USA, it is a massive problem that’s under-reported, according to Upstream.
One way this company combats crime is by creating a “digital twin” of each of the millions of vehicles it protects, Upstream knows when mileage goes backward, as well as other meaningful events like cyber-faking non-original crash parts when a vehicle is repaired.
Who are the criminals? Upstream says 63% of cyber incidents are due to Black Hat actors. Emergent threats associated with EV charging infrastructure is a new attack vector that threatens smart mobility and could expand to local grids.
What’s to be done? Upstream says “Next-generation regulations will focus on protecting sensitive data and EV charging infrastructure. Regulators are expected to shift their attention to drafting the next generation of automotive cybersecurity regulations as fleet-wide attacks targeting sensitive data and EV charging infrastructure rise, posing a serious threat to public safety.”
With operations in Ann Arbor, Michigan, Herzliya, Israel, London, England, Munich, Germany and Tokyo, Japan, it’s somewhat comforting to know that at over 25 million of the global vehicle fleet are under surveillance. Hopefully, one of them is mine.